Configuring Security Features
895
3. (Optional.) Click Browse to locate the target directory from your local system in the Target
Directory field.
The tool uses the file folder “Encrypted” as the target directory by default.
4. (Optional.) Mark the desired radio box in the AES Model field.
If you mark the Manual radio box, you can enter an AES key in the AES KEY field or click
Re-Generate to generate an AES key in the AES KEY field. The configuration file(s) will be
encrypted using the AES key in the AES KEY field.
If you mark the Auto Generate radio box, the configuration file(s) will be encrypted using
random AES key. The AES keys of configuration files are different.
Note
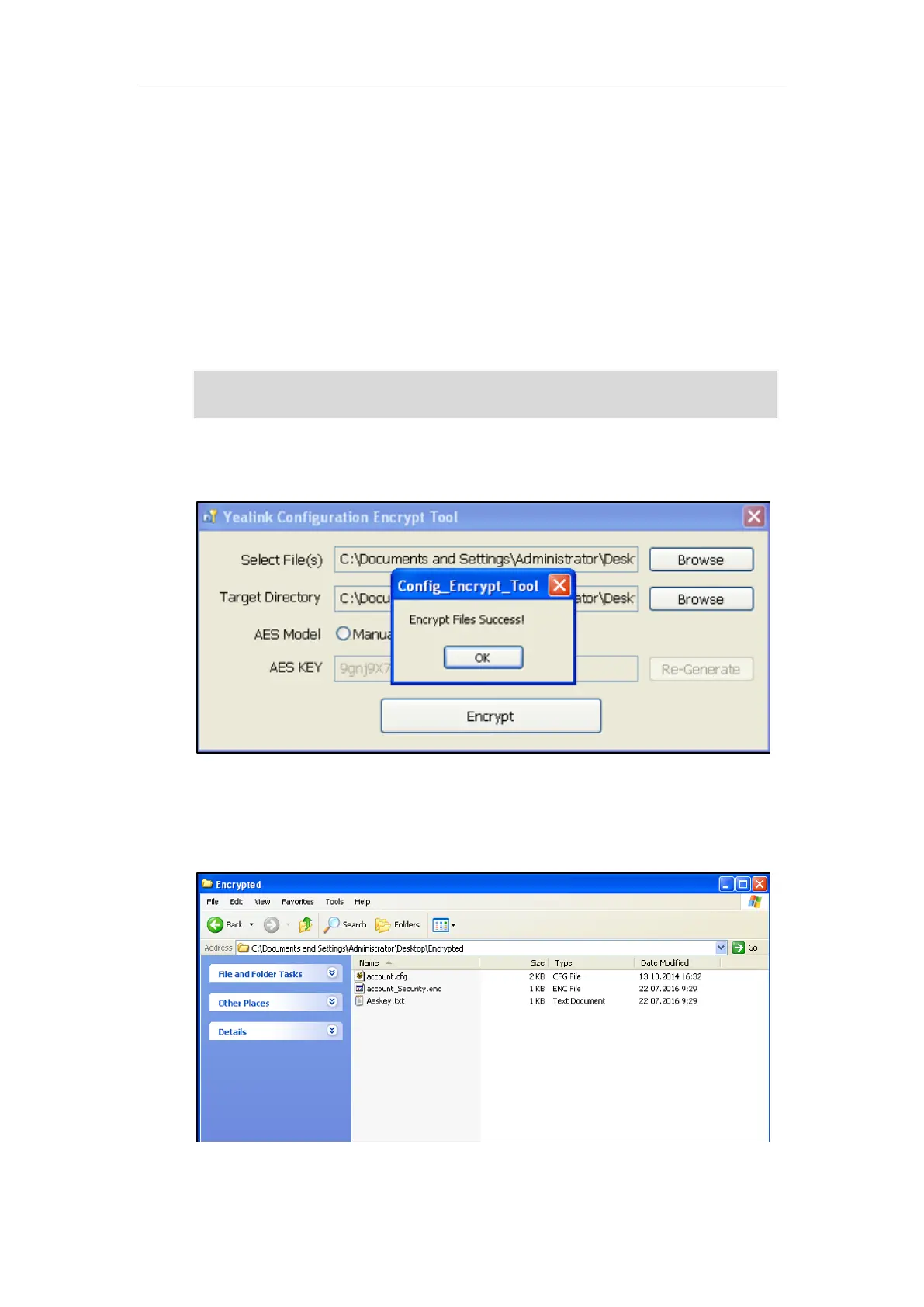
5. Click Encrypt to encrypt the configuration file(s).
6. Click OK.
The target directory will be automatically opened. You can find the encrypted CFG file(s),
encrypted key file(s) and an Aeskey.txt file storing plaintext AES key(s).
AES keys must be 16 characters and the supported characters contain: 0 ~ 9, A ~ Z, a ~ z and the
following special characters are also supported: # $ % * + , - . : = ? @ [ ] ^ _ { } ~.
 Loading...
Loading...