NOTES:
Duplicate key IDs are not permitted. NTP requests received by that do not contain an
authenticator containing a valid Key ID and MD5 message digest pair will be responded to,
but no authentication will be performed. An NTP request with valid authenticators results
in a valid NTP response with its own valid authenticator using the same Key ID provided in
the NTP request.
You may define the trusted Symmetric Keys that must be entered on both VersaSync, and
any network client with which VersaSync is to communicate. Only those keys for which the
“Trusted” box has been checked will appear in the dropdown menus on the NTP Refer-
ences screen.
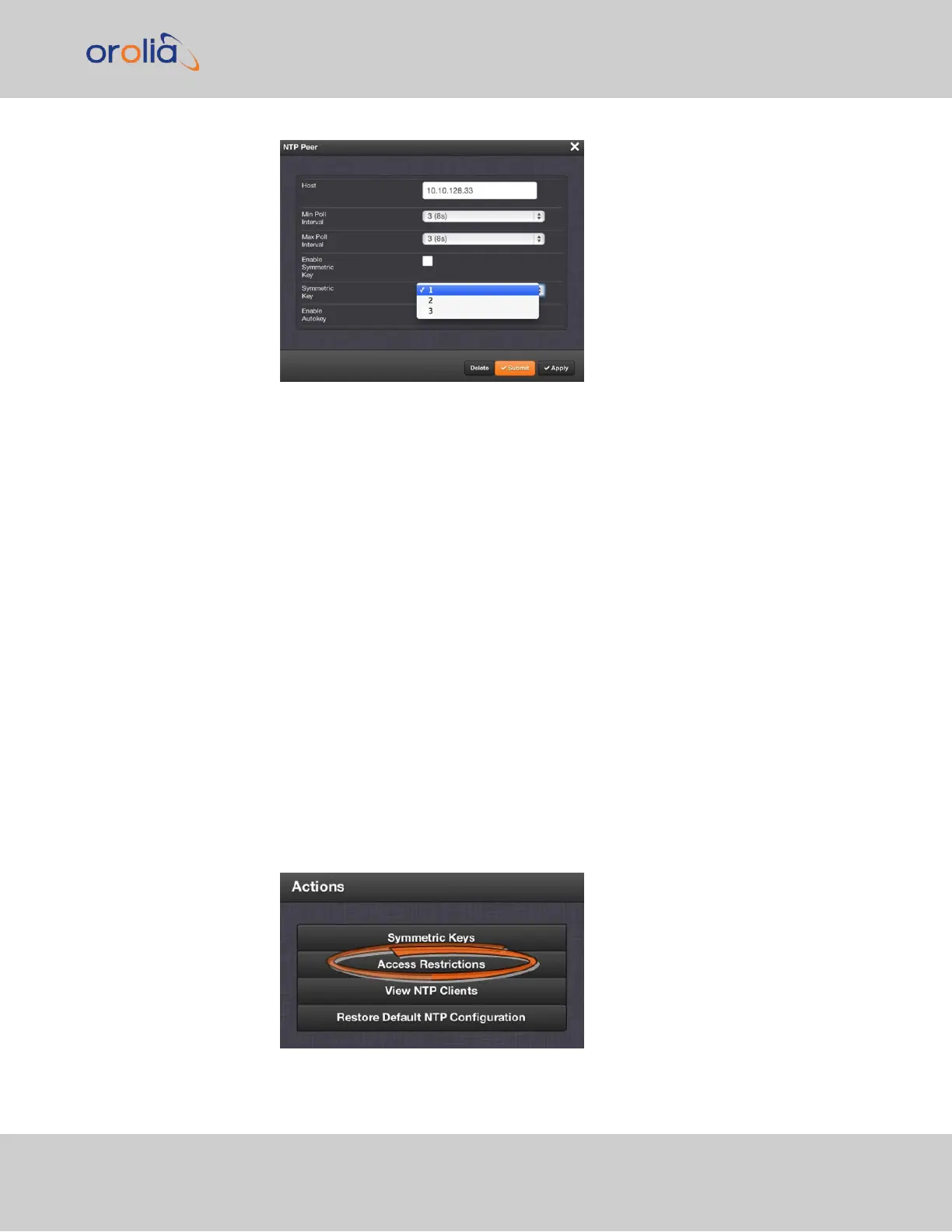
2.8.9.10 NTP Access Restrictions
Next to encrypted authentication by means of Symmetric Keys, NTP supports a list-based
means of access restriction, the use of which is also recommended to prevent fraudulent
or inadvertent manipulation of a time server.
To configure NTP Access Restrictions:
1.
Navigate to MANAGEMENT > NETWORK: NTP Setup.
2.
In the Actions panel, click Access Restrictions:
2.8 Configuring Network Settings
CHAPTER 2 • VersaSync User Manual Rev. 7.0
123
 Loading...
Loading...