1-6
Cisco ASA Series CLI Configuration Guide
Chapter 1 Configuring LAN-to-LAN IPsec VPNs
Creating an IKEv1 Transform Set
Step 5 Set the encryption key lifetime. The following example configures 43,200 seconds (12 hours):
hostname(config-ikev2-policy)# lifetime seconds 43200
hostname(config-ikev2-policy)#
Step 6 Enable IKEv2 on the interface named outside:
hostname(config)# crypto ikev2 enable outside
hostname(config)#
Step 7 To save your changes, enter the write memory command:
hostname(config)# write memory
hostname(config)#
Creating an IKEv1 Transform Set
An IKEv1 transform set combines an encryption method and an authentication method. During the IPsec
security association negotiation with ISAKMP, the peers agree to use a particular transform set to protect
a particular data flow. The transform set must be the same for both peers.
A transform set protects the data flows for the access list specified in the associated crypto map entry.
You can create transform sets in the ASA configuration, and then specify a maximum of 11 of them in
a crypto map or dynamic crypto map entry.
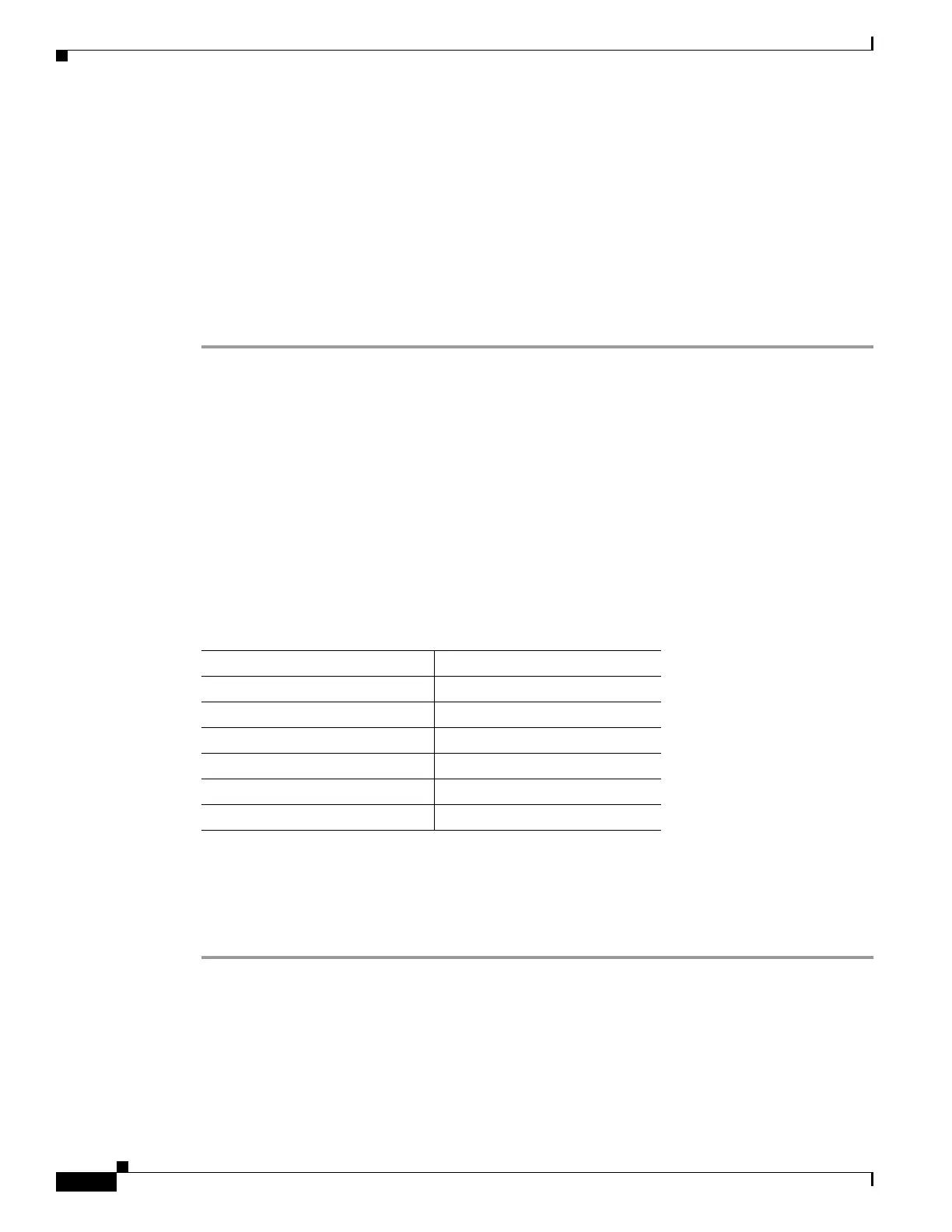
Table 1-1 lists valid encryption and authentication methods.
Tunnel Mode is the usual way to implement IPsec between two ASAs that are connected over an
untrusted network, such as the public Internet. Tunnel mode is the default and requires no configuration.
To configure a transform set, perform the following site-to-site tasks in either single or multiple context
mode:
Step 1 In global configuration mode enter the crypto ipsec ikev1 transform-set command. The following
example configures a transform set with the name FirstSet, esp-3des encryption, and esp-md5-hmac
authentication. The syntax is as follows:
crypto ipsec ikev1 transform-set transform-set-name encryption-method authentication-method
hostname(config)# crypto ipsec transform-set FirstSet esp-3des esp-md5-hmac
hostname(config)#
Table 1-1 Valid Encryption and Authentication Methods
Valid Encryption Methods Valid Authentication Methods
esp-des esp-md5-hmac
esp-3des (default) esp-sha-hmac (default)
esp-aes (128-bit encryption)
esp-aes-192
esp-aes-256
esp-null

 Loading...
Loading...