Access Control Lists
3-83
3
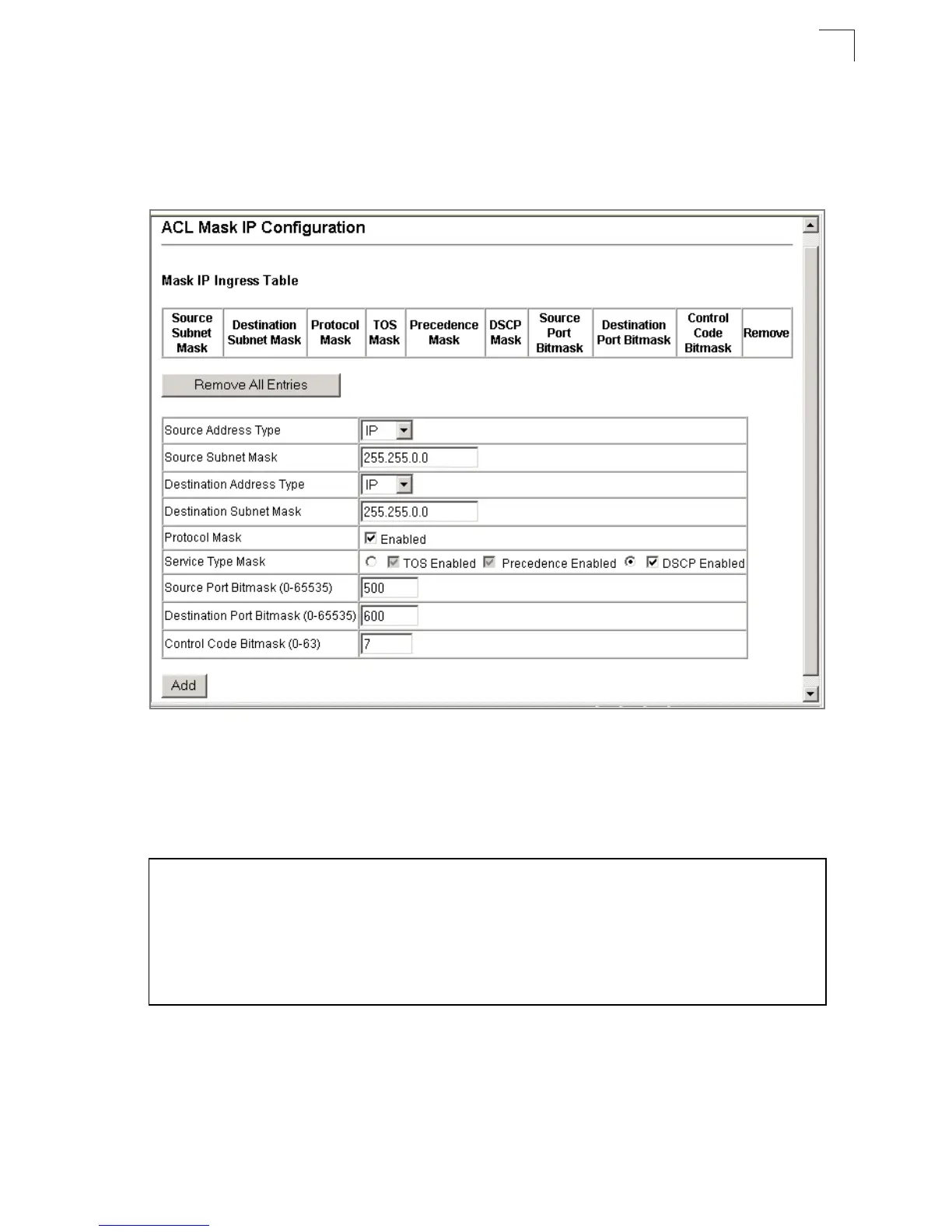
Web – Configure the mask to match the required rules in the IP ingress or egress
ACLs. Set the mask to check for any source or destination address, a specific host
address, or an address range. Include other criteria to search for in the rules, such
as a protocol type or one of the service types. Or use a bitmask to search for specific
protocol port(s) or TCP control code(s). Then click Add.
Figure 3-51. Configuring an IP based ACL
CLI – This shows that the entries in the mask override the precedence in which the
rules are entered into the ACL. In the following example, packets with the source
address 10.1.1.1 are dropped because the “deny 10.1.1.1 255.255.255.255” rule
has the higher precedence according the “mask host any” entry.
Console(config)#access-list ip standard A2 4-113
Console(config-std-acl)#permit 10.1.1.0 255.255.255.0 4-114
Console(config-std-acl)#deny 10.1.1.1 255.255.255.255
Console(config-std-acl)#exit
Console(config)#access-list ip mask-precedence in 4-117
Console(config-ip-mask-acl)#mask host any 4-118
Console(config-ip-mask-acl)#mask 255.255.255.0 any
Console(config-ip-mask-acl)#
 Loading...
Loading...











