Configuration Guide Configuring AAA
Local Authentication and Remote Server Authentication
Local authentication is the process where the entered passwords are verified by the database on the NAS.
Remote server authentication is the process where the entered passwords are checked by the database on a remote server.
It is mainly implemented by the RADIUS server and TACACS+ server.
Method List
AAA is implemented using different security methods. A method list defines a method implementation sequence. The method
list can contain one or more security protocols so that a standby method can take over the AAA service when the first method
fails. On Ruijie devices, the first method in the list is tried in the beginning and then the next is tried one by one if the previous
gives no response. This method selection process continues until a security method responds or all the security methods in
the list are tried out. Authentication fails if no method in the list responds.
A method list contains a series of security methods that will be queried in sequence to verify user identities. It allows you to
define one or more security protocols used for authentication, so that the standby authentication method takes over services
when the active security method fails. On Ruijie devices, the first method in the list is tried in the beginning and then the next
is tried one by one if the previous gives no response. This method selection process continues until a method responds or all
the methods in the method list are tried out. Authentication fails if no method in the list responds.
The next authentication method proceeds on Ruijie devices only when the current method does not respond. When a
method denies user access, the authentication process ends without trying other methods.
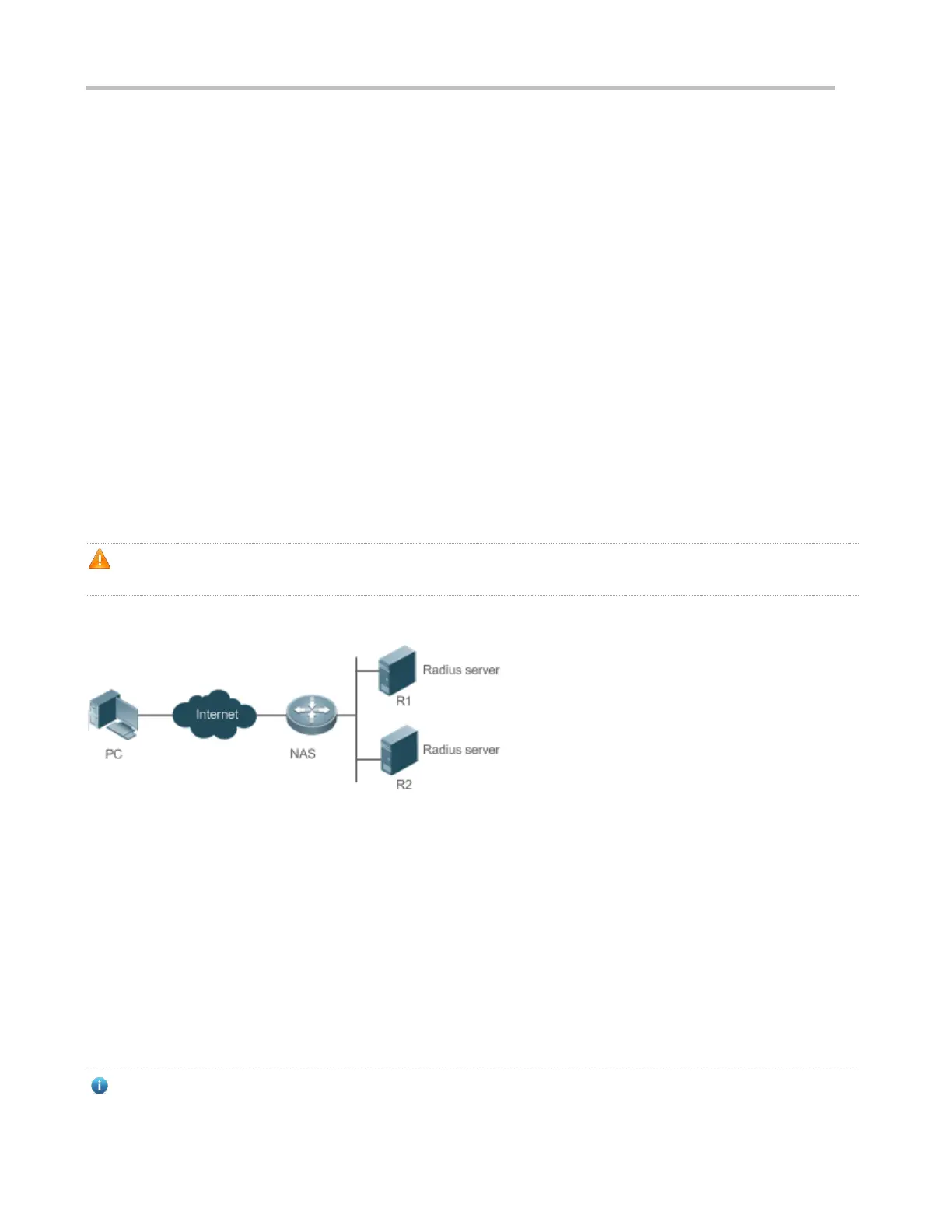
Figure 2-3
Figure 2-3 shows a typical AAA network topology, where two security servers (R1 and R2) and one NAS are deployed. The
NAS can be the client for the RADIUS servers.
Assume that the system administrator defines a method list, where the NAS selects R1 and R2 in sequence to obtain user
identity information and then accesses the local username database on the server. For example, when a remote PC user
initiates dial-up access, the NAS first queries the user's identity on R1. When the authentication on R1 is completed, R1
returns an Accept response to the NAS. Then the user is permitted to access the Internet. If R1 returns a Reject response,
the user is denied Internet access and the connection is terminated. If R1 does not respond, the NAS considers that the R1
method times out and continues to query the user's identity on R2. This process continues as the NAS keeps trying the
remaining authentication methods, until the user request is authenticated, rejected, or terminated. If all the authentication
methods are responded with Timeout, authentication fails and the connection will be terminated.
The Reject response is different from the Timeout response. The Reject response indicates that the user does not meet
the criteria of the available authentication database and therefore fails in authentication, and the Internet access

 Loading...
Loading...