Configuration Guide Configuring DHCP Snooping
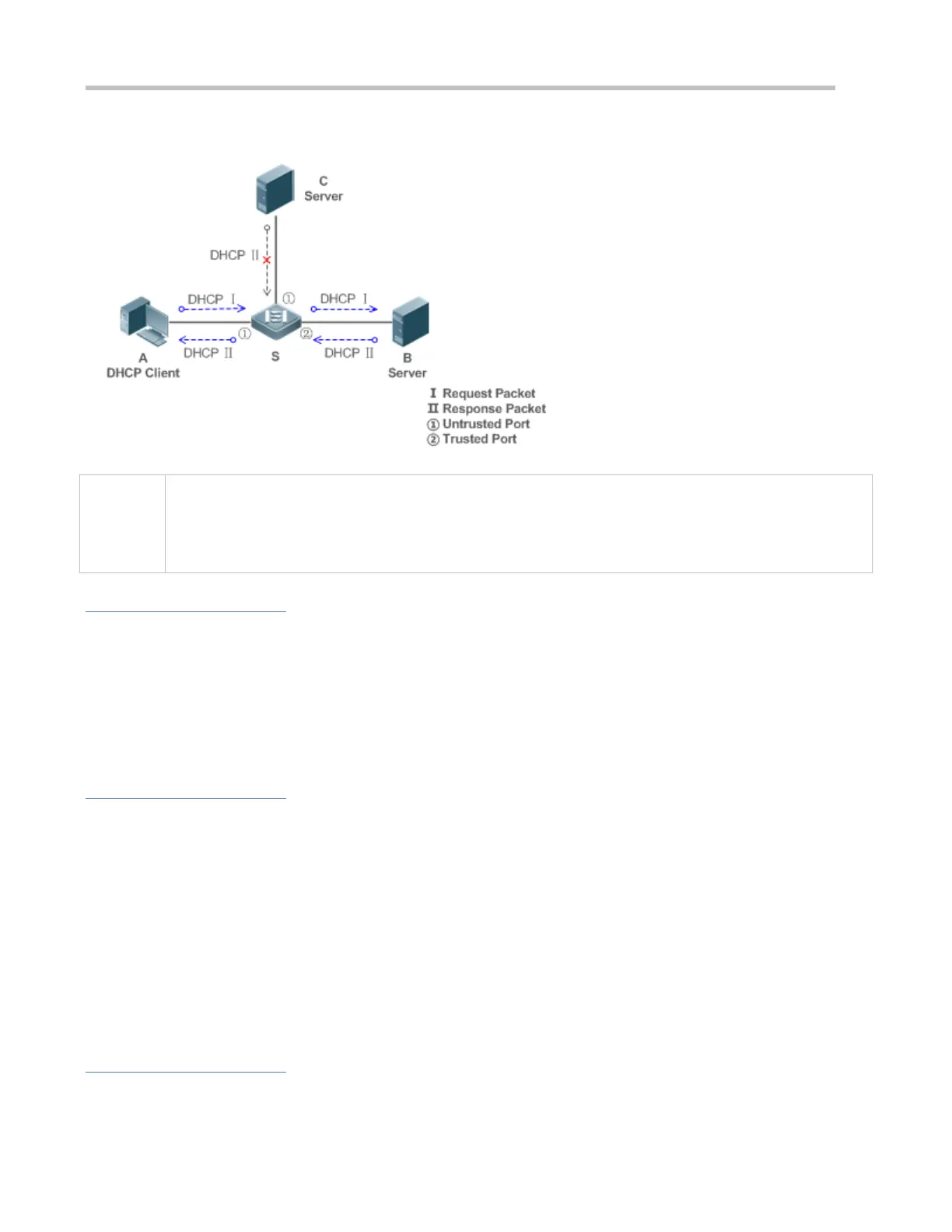
Figure 8-1
S is an access device.
A is a user PC.
B is a DHCP server within the controlled area.
C is a DHCP server out of the controlled area.
Deployment
Enable DHCP Snooping on S to realize DHCP packet monitoring.
Set the port on S connecting to B as trusted to transfer response packets.
Set the rest of ports on S as untrusted to filter response packets.
8.2.2 Guarding Against DHCP Packet Flooding
Scenario
Potential malicious DHCP clients in a network may send high-rate DHCP packets. As a result, legitimate users cannot obtain
IP addresses, and access devices are highly loaded or even break down. It is necessary to take actions to ensure network
stability.
With the DHCP Snooping rate limit function for DHCP packets, a DHCP client can only send DHCP request packets at a rate
below the limit.
The request packets from a DHCP client are sent at a rate below the limit.
Packets sent at rates beyond the limit will be discarded.
Enable DHCP Snooping correlation with ARP, and delete the non-existing entries.
Deployment
Enable DHCP Snooping on S to realize DHCP monitoring.

 Loading...
Loading...