Configuration Guide Configuring RADIUS
Authorization, and Accounting
Services for Access Users
network, to prevent unauthorized access or operations.
Forcing Users to Go Offline
The server forces an authenticated user to go offline.
3.2.1 Providing Authentication, Authorization, and Accounting Services for Access
Users
Scenario
RADIUS is typically applied in the authentication, authorization, and accounting of access users. A network device serves as
a RADIUS client and transmits user information to a RADIUS server. After completing processing, the RADIUS server
returns the authentication acceptance/authentication rejection/accounting response information to the RADIUS client. The
RADIUS client performs processing on the access user according to the response from the RADIUS server.
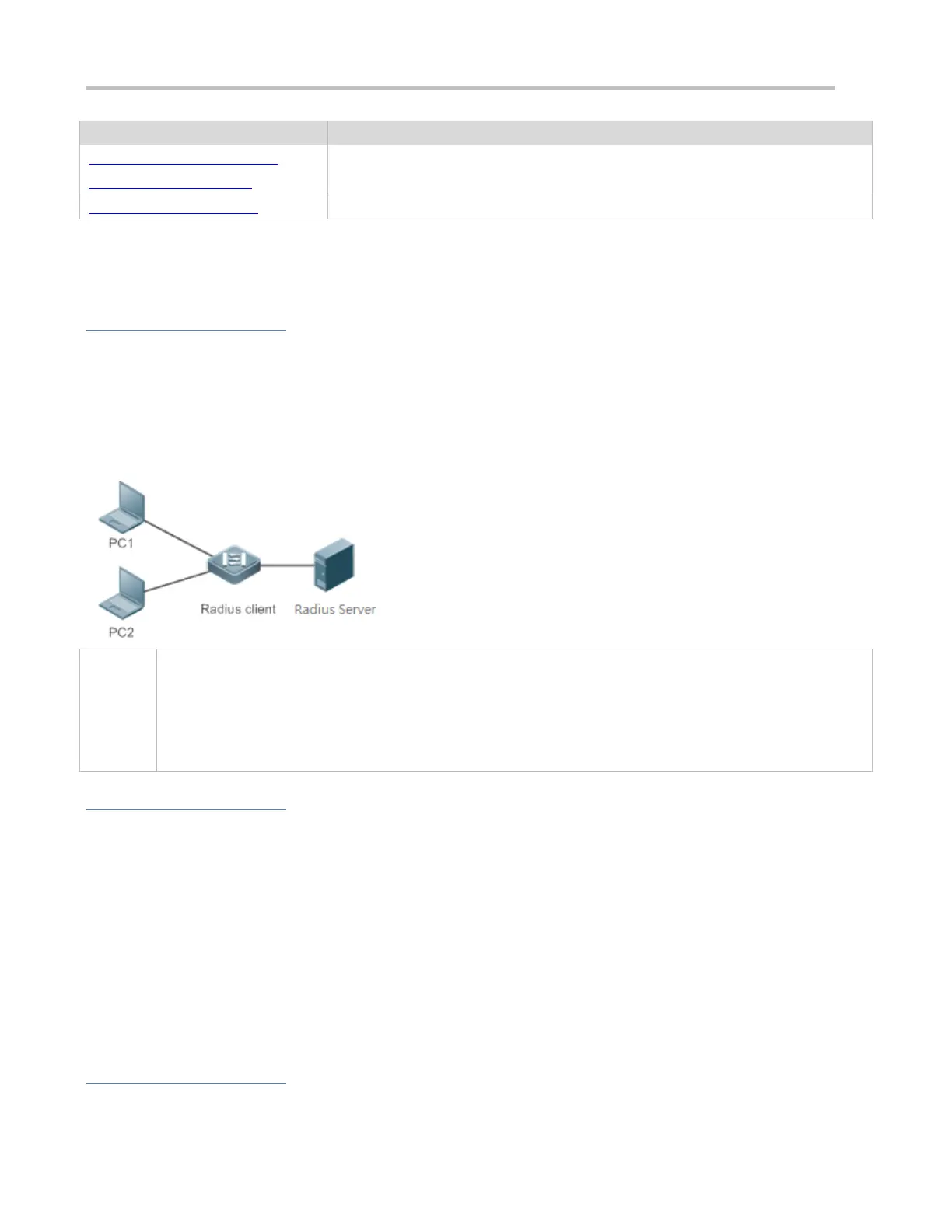
Figure 3-1 Typical RADIUS Networking Topology
PC 1 and PC 2 are connected to the RADIUS client as access users in wired or wireless mode, and initiate
authentication and accounting requests.
The RADIUS client is usually an access switch or aggregate switch.
The RADIUS server can be a component built in the Windows 2000/2003, Server (IAS), or UNIX operating
system or dedicated server software provided by vendors.
Deployment
Configure access device information on the RADIUS server, including the IP address and shared key of the access
devices.
Configure the AAA method list on the RADIUS client.
Configure the RADIUS server information on the RADIUS client, including the IP address and shared key.
Enable access control on the access port of the RADIUS client.
Configure the network so that the RADIUS client communicates with the RADIUS server successfully.
3.2.2 Forcing Users to Go Offline
Scenario
The RADIUS server forces authenticated online users to go offline for the sake of management.

 Loading...
Loading...