Configuration Guide Configuring SSH
Use the authentication, authorization and accounting (AAA) mode for SSH user
authentication.
SSH Public Key Authentication
Use the public key authentication for SSH user authentication.
Use the Secure Copy (SCP) commands on the client to exchange data with the SSH
server.
14.2.1 SSH Device Management
Scenario
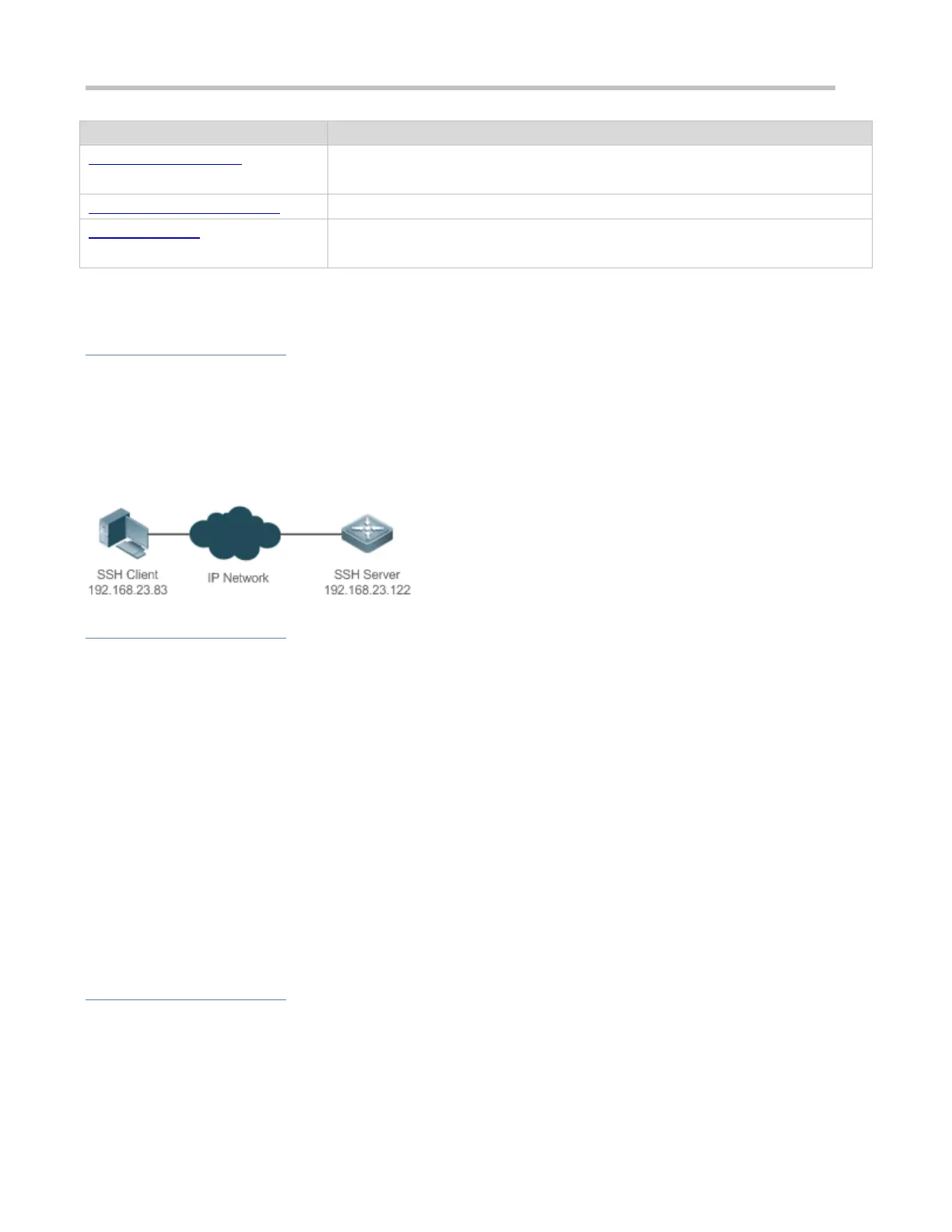
You can use SSH to manage devices on the precondition that the SSH server function is enabled. By default, this function is
disabled. The Telnet component that comes with the Windows system does not support SSH. Therefore, a third-party client
software must be used. Currently, well-compatible software includes PuTTY, Linux, and SecureCRT. The following takes the
PuTTY as an example to introduce the configurations of the SSH client. Figure 14-1 shows the network topology.
Figure 14-1 Networking Topology of SSH Device Management
Deployment
Configure the SSH client as follows:
Start the PuTTY software.
On the Session option tab of PuTTY, type in the host IP address of the SSH server and SSH port number 22, and
select the connection type SSH.
On the SSH option tab of PuTTY, select the preferred SSH protocol version 2.
On the SSH authentication option tab of PuTTY, select the authentication method Attempt "keyboard-interactive"
auth.
Click Open to connect to the SSH server.
Type in the correct user name and password to enter the terminal login interface.
14.2.2 SSH Local Line Authentication
Scenario
SSH clients can use the local line password authentication mode, as shown in Figure 14-2. To ensure security of data
exchange, PC 1 and PC 2 function as the SSH clients, and use the SSH protocol to log in to the network device where the
SSH server function is enabled. The requirements are as follows:
SSH users use the local line password authentication mode.

 Loading...
Loading...