Configuration Guide Configuring DHCP Snooping
Deployment
The same as that in the section "Guarding Against IP/MAC Spoofing".
8.2.6 Detecting ARP Attacks
Scenario
Check the ARP packets from untrusted ports and filter out the ARP packets unmatched with the assignments of the DHCP
server.
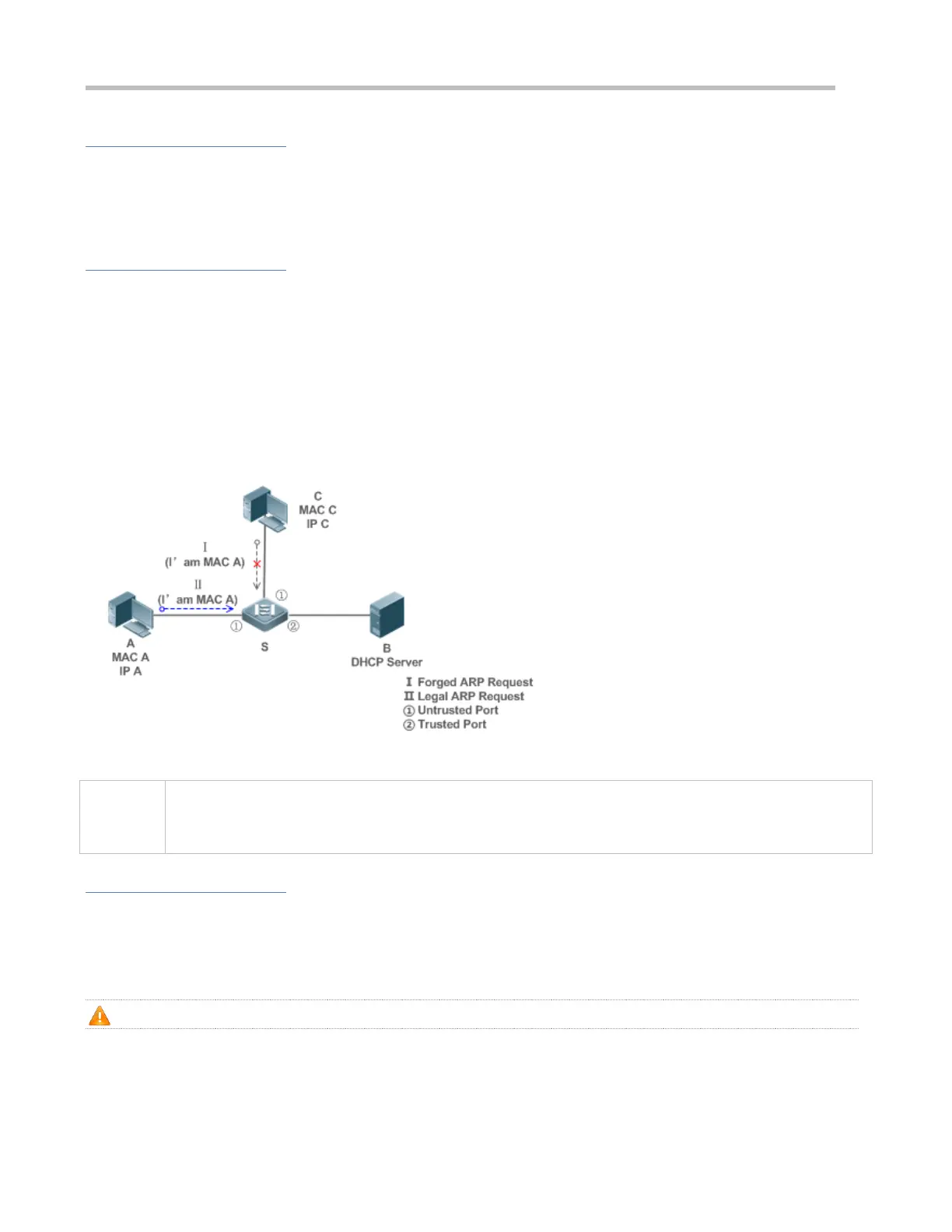
For example, in the following figure, the ARP packets sent from DHCP clients will be checked.
The ports receiving ARP packets, the layer-2 MAC addresses, and the source MAC addresses of ARP packets senders
shall be consistent with the DHCP Snooping histories.
Figure 8-4
S is an access device.
A and C are user PCs.
B is a DHCP server within the controlled area.
Deployment
Enable DHCP Snooping on S to realize DHCP monitoring.
Set all downlink ports on the S as untrusted.
Enable IP Source Guard and ARP Check on all the untrusted ports on S to realize ARP packet filtering.
All the above security control functions are only effective to DHCP Snooping untrusted ports.

 Loading...
Loading...