xStack® DGS-3120 Series Layer 3 Managed Gigabit Ethernet Switch Web UI Reference Guide
368
The type of MAC address in the forwarding database table.
Click the Find button to locate a specific entry based on the information entered.
Click the Clear button to clear all the entries based on the information entered.
Click the Show All button to display all the existing entries.
Click the Clear All button to remove all the entries listed.
Click the Delete button to remove the specific entry.
Enter a page number and click the Go button to navigate to a specific page when multiple pages exist.
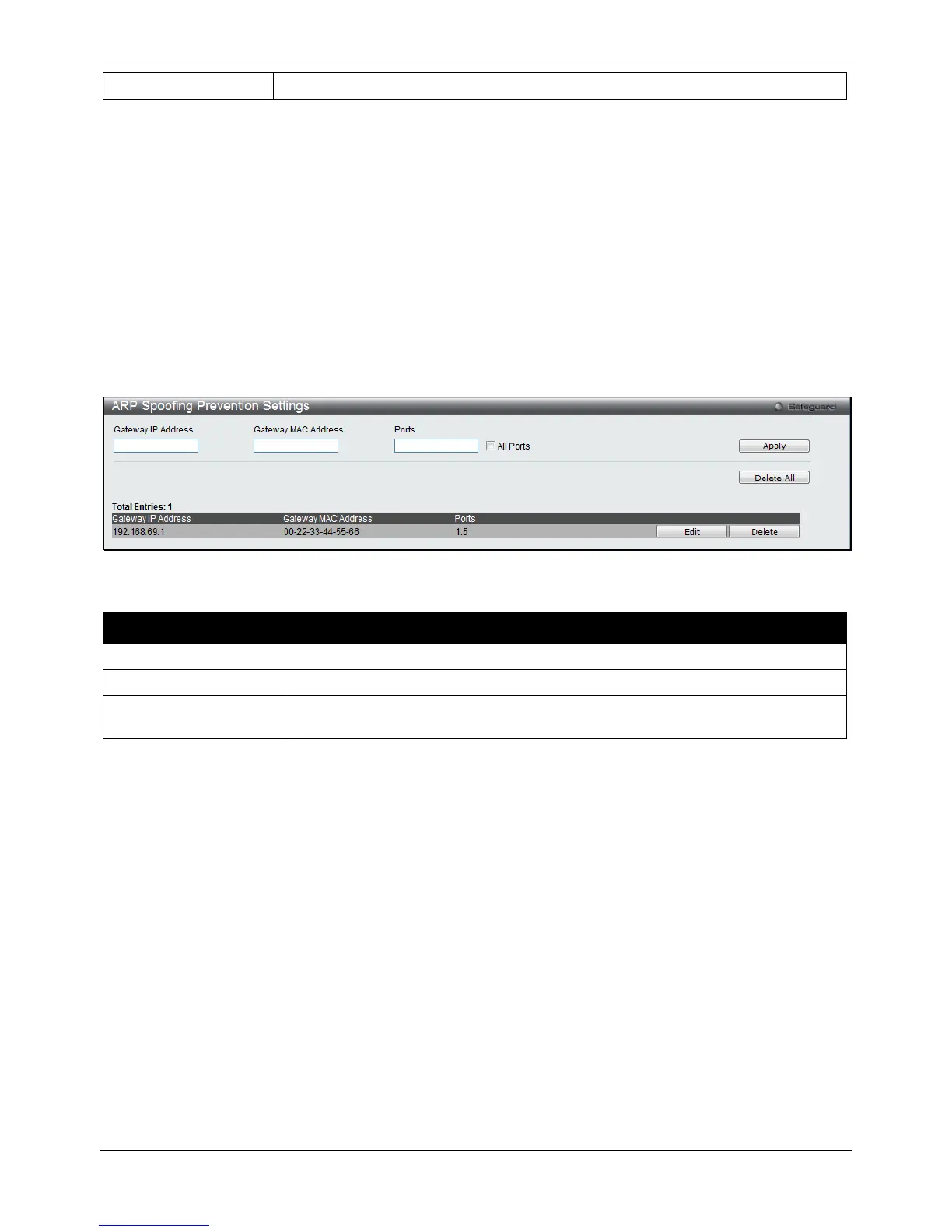
ARP Spoofing Prevention Settings
The user can configure the spoofing prevention entry to prevent spoofing of MAC for the protected gateway. When
an entry is created, those ARP packets whose sender IP matches the gateway IP of an entry, but either its sender
MAC field or source MAC field does not match the gateway MAC of the entry will be dropped by the system.
To view this window, click Security > ARP Spoofing Prevention Settings as shown below:
Figure 8-62 ARP Spoofing Prevention Settings window
The fields that can be configured are described below:
Parameter Description
Enter the gateway IP address to help prevent ARP Spoofing.
Enter the gateway MAC address to help prevent ARP Spoofing.
Ports
Enter the port numbers that this feature applies to. Alternatively the user can select
All Ports to apply this feature to all the ports of the switch.
Click the Apply button to accept the changes made.
Click the Delete All button to remove all the entries listed.
Click the Edit button to re-configure the specific entry.
Click the Delete button to remove the specific entry.
BPDU Attack Protection
This window is used to configure the BPDU protection function for the ports on the switch. In generally, there are
two states in BPDU protection function. One is normal state, and another is under attack state. The under attack
state have three modes: drop, block, and shutdown. A BPDU protection enabled port will enter an under attack
state when it receives one STP BPDU packet. And it will take action based on the configuration. Thus, BPDU
protection can only be enabled on the STP-disabled port.
BPDU protection has a higher priority than the FBPDU setting configured by configure STP command in the
determination of BPDU handling. That is, when FBPDU is configured to forward STP BPDU but BPDU protection is
enabled, then the port will not forward STP BPDU.
BPDU protection also has a higher priority than the BPDU tunnel port setting in determination of BPDU handling.
That is, when a port is configured as BPDU tunnel port for STP, it will forward STP BPDU. But if the port is BPDU
protection enabled. Then the port will not forward STP BPDU.
 Loading...
Loading...











