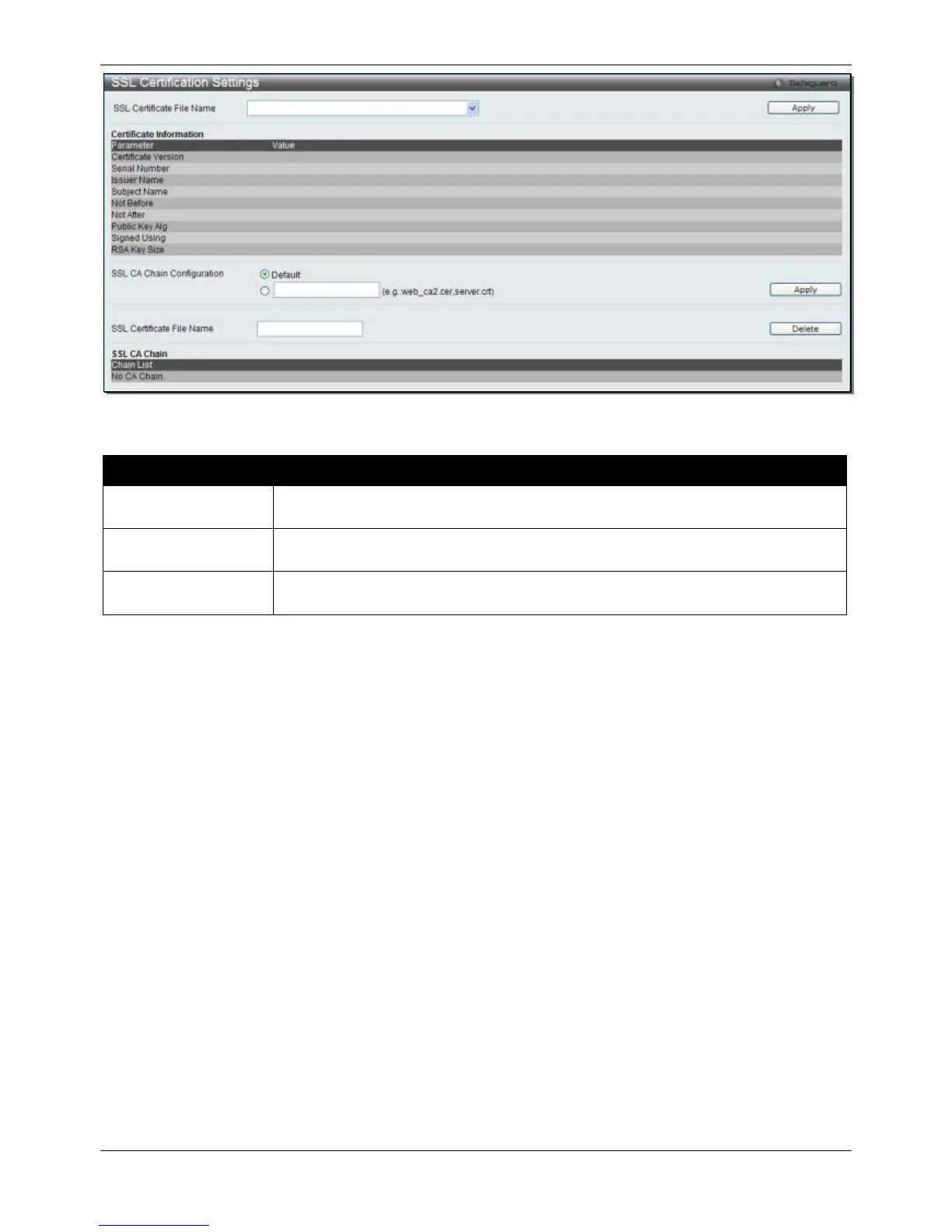
Enter an SSL certificate file name to be deleted.
Click the Apply button to accept the changes made for each individual section.
Click the Delete button to remove the specific entry.
SSH
SSH is an abbreviation of Secure Shell, which is a program allowing secure remote login and secure network
services over an insecure network. It allows a secure login to remote host computers, a safe method of executing
commands on a remote end node, and will provide secure encrypted and authenticated communication between
two non-trusted hosts. SSH, with its array of unmatched security features is an essential tool in today’s networking
environment. It is a powerful guardian against numerous existing security hazards that now threaten network
communications.
The steps required to use the SSH protocol for secure communication between a remote PC (the SSH client) and
the Switch (the SSH server) are as follows:
Chapter 1 Create a user account with admin-level access using the User Accounts window. This is identical
to creating any other admin-level User Account on the Switch, including specifying a password. This password is
used to logon to the Switch, once a secure communication path has been established using the SSH protocol.
Chapter 2 Configure the User Account to use a specified authorization method to identify users that are
allowed to establish SSH connections with the Switch using the SSH User Authentication Mode window. There
are three choices as to the method SSH will use to authorize the user, which are Host Based, Password, and
Public Key.
Chapter 3 Configure the encryption algorithm that SSH will use to encrypt and decrypt messages sent
between the SSH client and the SSH server, using the SSH Authentication Method and Algorithm Settings window.
Chapter 4 Finally, enable SSH on the Switch using the SSH Configuration window.
After completing the preceding steps, a SSH Client on a remote PC can be configured to manage the Switch using
a secure, in band connection.
 Loading...
Loading...











