Firewall Policy Configuring firewall policies
FortiGate Version 4.0 MR1 Administration Guide
01-410-89802-20090903 399
http://docs.fortinet.com/ • Feedback
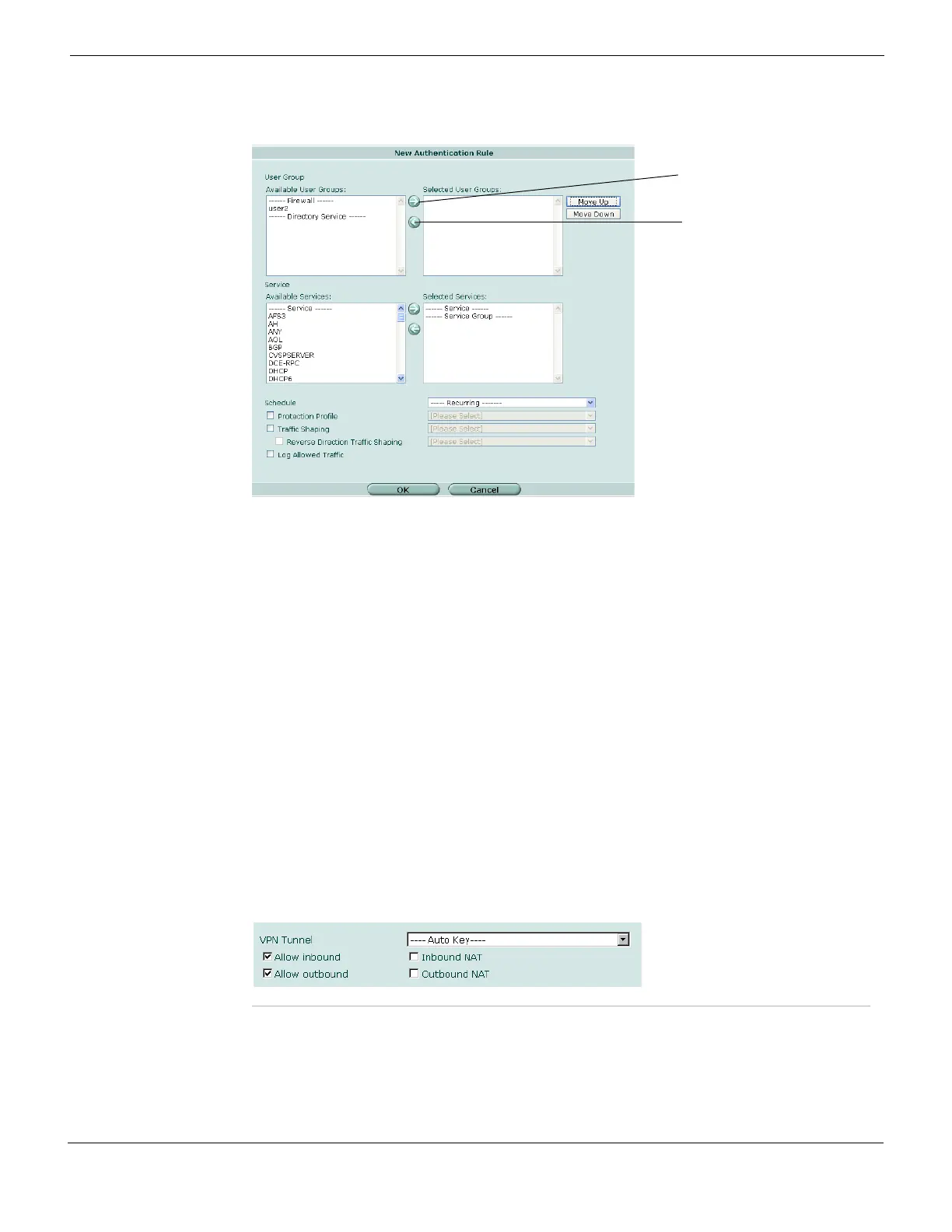
Figure 211: Creating identity-based firewall policies
6 From the Available User Groups list, select one or more user groups that must
authenticate to be allowed to use this policy. Select the right arrow to move the
selected user groups to the Selected User Groups list.
7 Select services in the Available Services list and then select the right arrow to move
them to the Selected Services list.
8 Select a schedule from the Schedule drop-down list. There is no default.
9 Optionally, select a Protection Profile, enable User Authentication Disclaimer or Log
Allowed Traffic.
10 Optionally, select Traffic Shaping and choose a traffic shaper.
11 Select OK.
IPSec firewall policy options
In a firewall policy (see “Configuring firewall policies” on page 391), the following
encryption options are available for IPSec. To configure these options, go to Firewall >
Policy, select Create New to add a firewall policy, or in the row corresponding to an
existing firewall policy, select Edit. Make sure that Action is set to IPSEC. Enter the
information in the following table and select OK.
Figure 212: IPSEC encryption policy
VPN Tunnel Select the VPN tunnel name defined in the phase 1 configuration. The specified
tunnel will be subject to this firewall encryption policy.
Allow Inbound Select to enable traffic from a dialup client or computers on the remote private
network to initiate the tunnel.
Allow outbound Select to enable traffic from computers on the local private network to initiate
the tunnel.
 Loading...
Loading...











