IPSec VPN Auto Key
FortiGate Version 4.0 MR1 Administration Guide
01-410-89802-20090903 619
http://docs.fortinet.com/ • Feedback
Creating a new phase 2 configuration
After IPSec phase 1 negotiations end successfully, you begin phase 2. You configure the
phase 2 parameters to define the algorithms that the FortiGate unit may use to encrypt
and transfer data for the remainder of the session. During phase 2, you select specific
IPSec security associations needed to implement security services and establish a tunnel.
The basic phase 2 settings associate IPSec phase 2 parameters with the phase 1
configuration that specifies the remote end point of the VPN tunnel. In most cases, you
need to configure only basic phase 2 settings.
To configure phase 2 settings, go to VPN > IPSEC > Auto Key (IKE) and select Create
Phase 2. For information about how to choose the correct phase 2 settings for your
particular situation, see the FortiGate IPSec VPN User Guide.
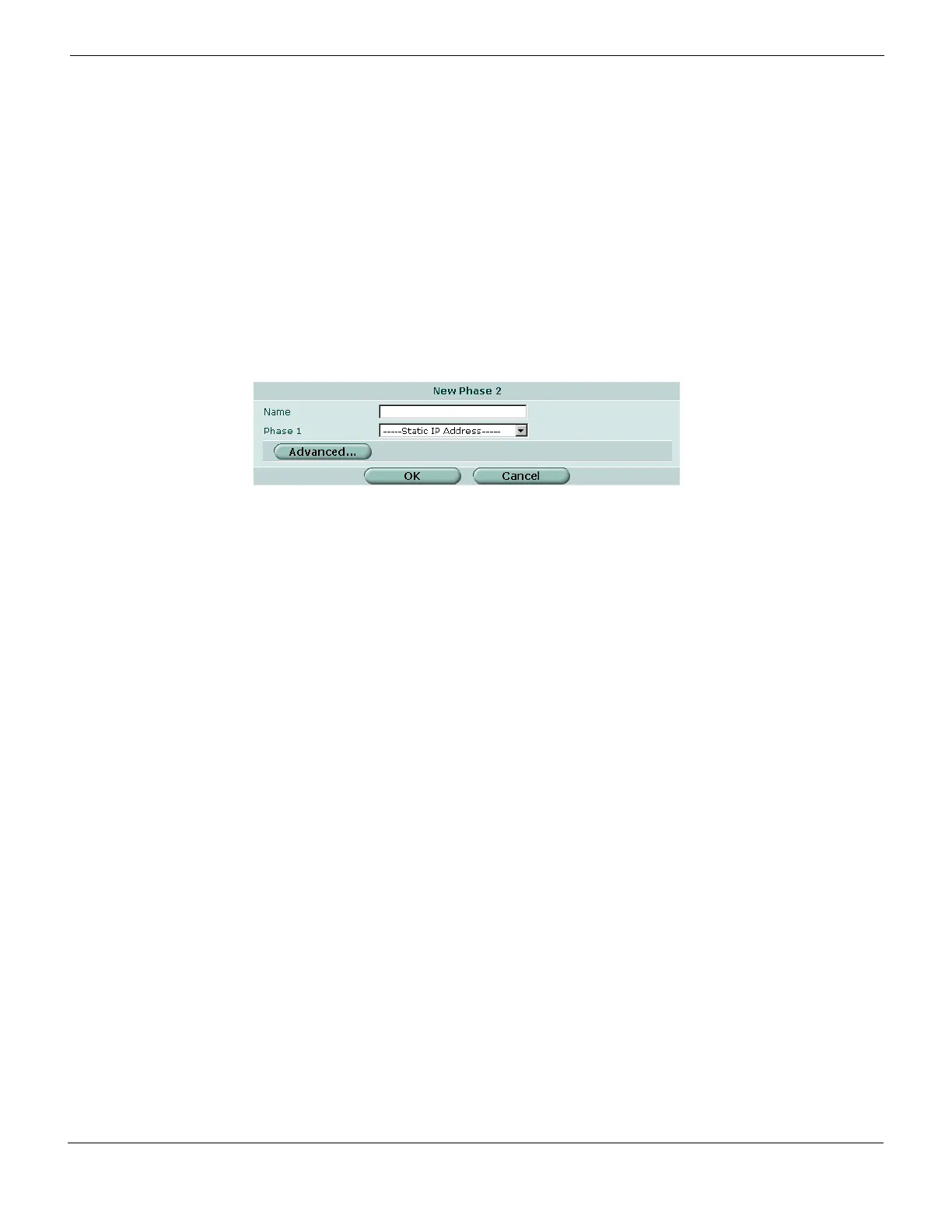
Figure 380: New Phase 2
Defining phase 2 advanced settings
In phase 2, the FortiGate unit and the VPN peer or client exchange keys again to establish
a secure communication channel between them. You select the encryption and
authentication algorithms needed to generate keys for protecting the implementation
details of Security Associations (SAs). These are called P2 Proposal parameters. The
keys are generated automatically using a Diffie-Hellman algorithm.
You can use a number of additional advanced phase 2 settings to enhance the operation
of the tunnel. To modify IPSec phase 2 advanced parameters, go to VPN > IPSEC
Auto Key (IKE), select Create Phase 2, and then select Advanced. For information about
how to choose the correct advanced phase 2 settings for your particular situation, see the
FortiGate IPSec VPN User Guide.
Name Type a name to identify the phase 2 configuration.
Phase 1 Select the phase 1 tunnel configuration. For more information, see “Creating a
new phase 1 configuration” on page 614. The phase 1 configuration describes
how remote VPN peers or clients will be authenticated on this tunnel, and how the
connection to the remote peer or client will be secured.
Advanced Define advanced phase 2 parameters. For more information, see “Defining
phase 2 advanced settings” on page 619.
 Loading...
Loading...











