Installation and Maintenance Manual - Aastra 5000 AMT/PTD/PBX/0058/4/6/EN
Appendices 01/2011 Page 493
11.3 CONFIGURING THE FIREWALL FOR ACS
The installation of Red Hat Enterprise Linux 5 is described in the “Red Hat Installation
Guide” (see reference documents). For a simplified installation, this document
recommends that the firewall be deactivated.
For the ACS application, the use of a firewall is, nevertheless, recommended in
order to secure the network. In this case, the firewall must be configured in such a
way that it will not filter the ports required by the application to work properly.
This paragraph specifies the Red Hat configuration elements required for ACS installation.
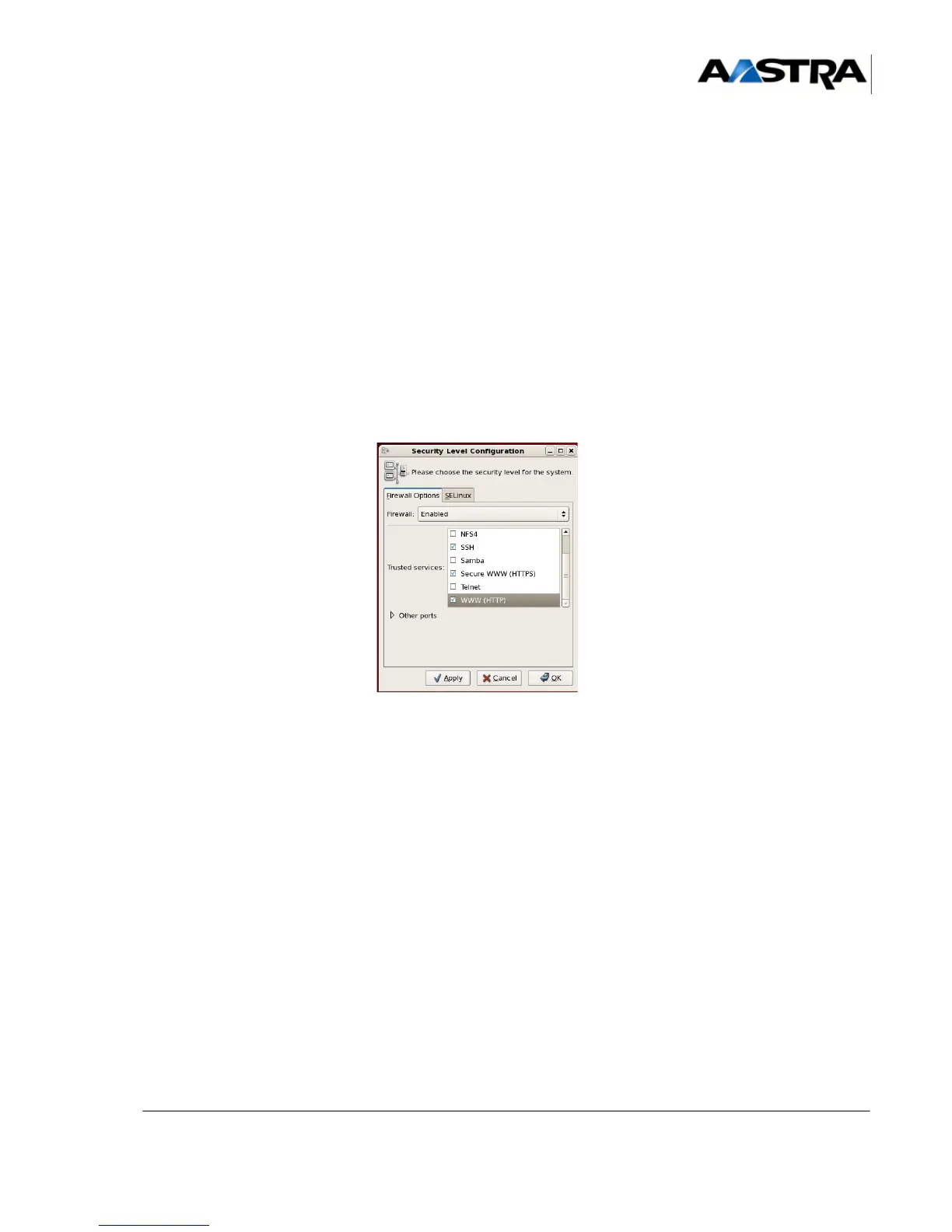
To access the firewall configuration menu:
Click System > Administration > Security level and firewall.
In the firewall options tab:
1 Select the firewall option Active.
The selection areas become accessible.
2 In the Trusted services list, tick the minimum services to be activated:
• FTP
• SSH
• HTTP
• HTTPS
3 Click the Other ports title bar.
4 To add other ports, click Add.
An Add port input window opens.
5 In this window, enter the port number and select a protocol then click Confirm.
The port is added to the list.
6 When all the ports are configured, click Apply then Confirm.
The firewall is configured.
 Loading...
Loading...