331
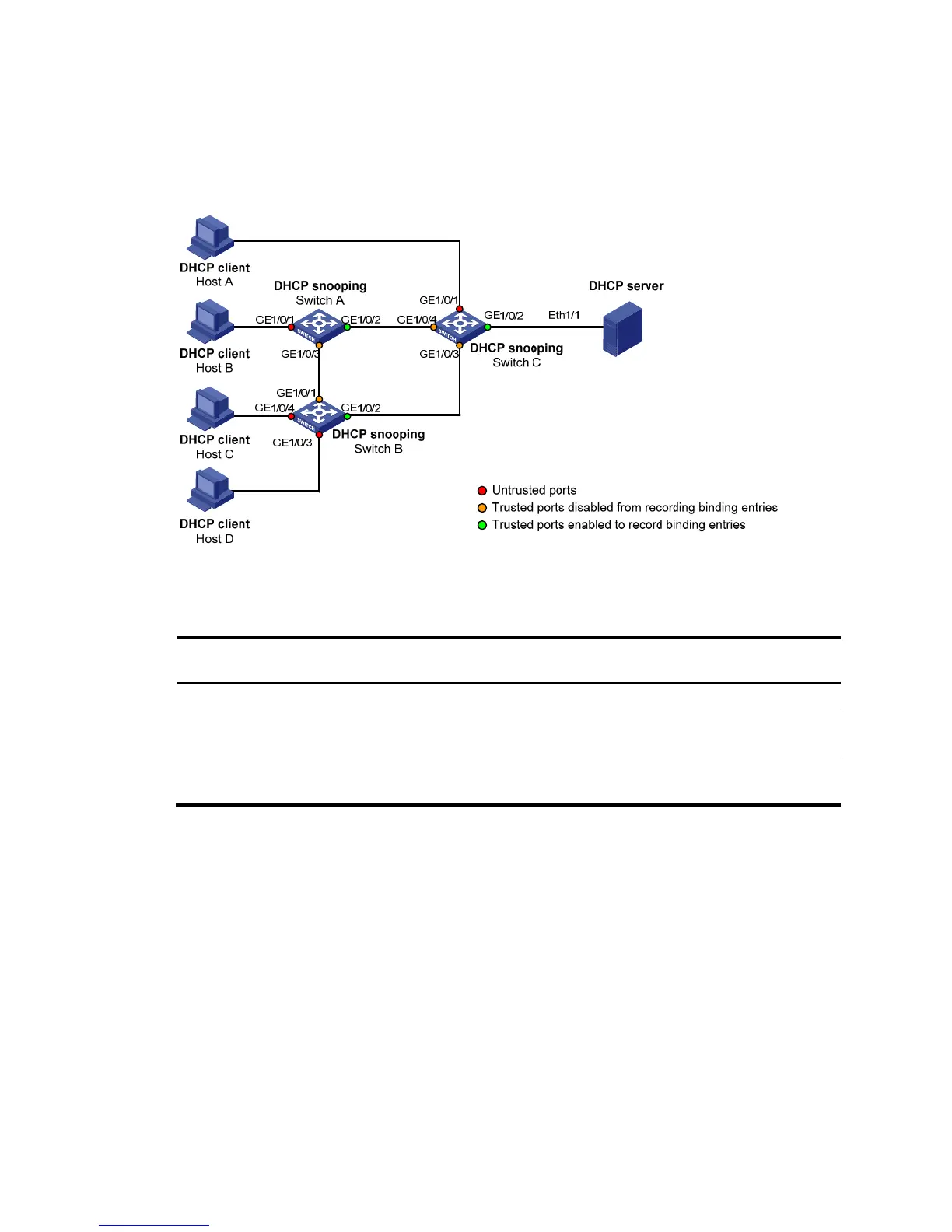
In a cascaded network as shown in Figure 299, configure each DHCP snooping device's ports
connected to other DHCP snooping devices as trusted ports. To save system resources, you can disable
the untrusted ports that are not directly connected to DHCP clients from generating DHCP snooping
entries.
Figure 299 Trusted ports and untrusted ports in a cascaded network
Table 98 describes roles of the ports shown in Figure 299.
Table 98 Roles of ports
Device Untrusted port
Trusted port disabled from
recordin
Switch A GigabitEthernet 1/0/1 GigabitEthernet 1/0/3 GigabitEthernet 1/0/2
Switch B
GigabitEthernet 1/0/3 and
GigabitEthernet 1/0/4
GigabitEthernet 1/0/1 GigabitEthernet 1/0/2
Switch C GigabitEthernet 1/0/1
GigabitEthernet 1/0/3 and
GigabitEthernet 1/0/4
GigabitEthernet 1/0/2
DHCP snooping support for Option 82
Option 82 records the location information of the DHCP client. The administrator can locate the DHCP
client to further implement security control and accounting. For more information, see "Relay agent
opti
on (Option 82))."
If DHCP snooping supports Option 82, it will handle a client’s request according to the contents defined
in Option 82, if any. The handling strategies are described in the table below.
If a reply returned by the DHCP server contains Option 82, the DHCP snooping device will remove the
Option 82 before forwarding the reply to the client. If the reply contains no Option 82, the DHCP
snooping device forwards it directly.
 Loading...
Loading...











