450
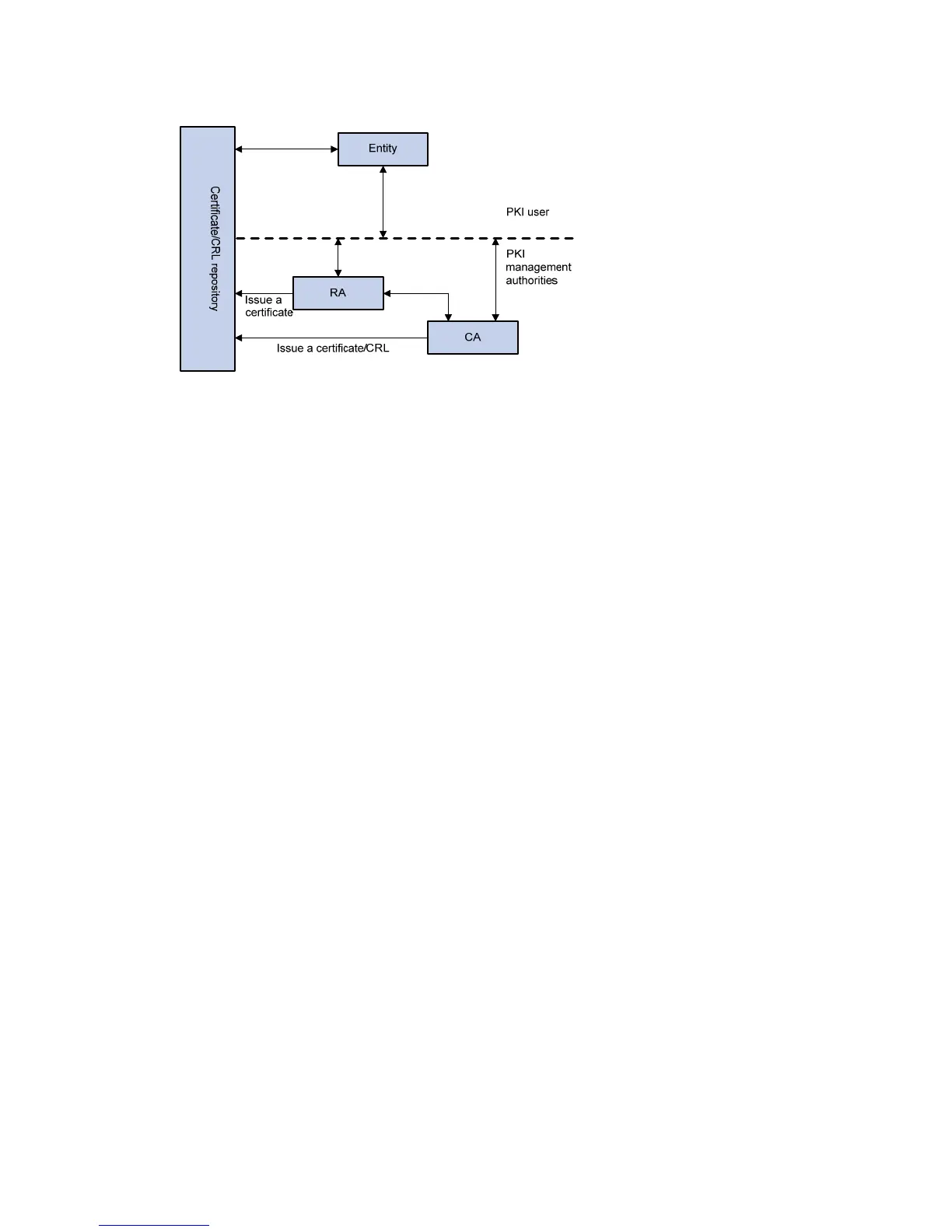
Figure 432 PKI architecture
• PKI entity—A PKI entity is an end user or host using PKI certificates. The PKI entity can be an
operator, an organization, a device like a router or a switch, or a process running on a computer.
• CA—A CA is a trusted authority that issues and manages digital certificates. A CA issues
certificates, defines the certificate validity periods, and revokes certificates by publishing CRLs.
• RA—A registration authority (RA) is an extended part of a CA or an independent authority. An RA
can implement functions including identity authentication, CRL management, key pair generation
and key pair backup. It only examines the qualifications of users; it does not sign certificates.
Sometimes, a CA assumes the registration management responsibility and no independent RA
exists. The PKI standard recommends that an independent RA be used for registration management
to achieve higher security of application systems.
• Repository—A PKI repository can be a Lightweight Directory Access Protocol (LDAP) server or a
common database. It stores and manages information like certificate requests, certificates, keys,
CRLs and logs, and it provides a simple query function.
LDAP is a protocol for accessing and managing PKI information. An LDAP server stores user
information and digital certificates from the RA server and provides directory navigation service.
From an LDAP server, an entity can retrieve digital certificates of its own and other entities.
PKI applications
The PKI technology can meet the security requirements of online transactions. As an infrastructure, PKI
has a wide range of applications. Here are some application examples.
• VPN—A VPN is a private data communication network built on the public communication
infrastructure. A VPN can leverage network layer security protocols (for example, IPsec) in
conjunction with PKI-based encryption and digital signature technologies for confidentiality.
• Secure emails—PKI can address the email requirements for confidentiality, integrity, authentication,
and non-repudiation. A common secure email protocol is Secure/Multipurpose Internet Mail
Extensions (S/MIME), which is based on PKI and allows for transfer of encrypted mails with
signature.
• Web security—The SSL protocol can be used to establish a secure connection between a client and
a Web server. During the SSL handshake, both parties can use PKI to identity the peer identity by
digital certificates.
 Loading...
Loading...











