Administrator’s Guide for SIP-T58V/T58A/T56A/CP960 IP Phones
328
Permitted
Values
0-Disabled, the MAC-local CFG file will be uploaded unencrypted and will replace the one (encrypted or
unencrypted) stored on the server if you have configured to back up the MAC-local CFG file to the server
by the parameter “static.auto_provision.custom.sync”.
1-Enabled, the MAC-local CFG file will be uploaded encrypted and will replace the one (encrypted or
unencrypted) stored on the server if you have configured to back up the MAC-local CFG file to the server
by the parameter “static.auto_provision.custom.sync”. The plaintext AES key is configured by the para-
meter “static.auto_provision.aes_key_16.mac”.
Default 0
[1]
X is an activation code ID. For all phones, X=1-50.
[2]
If you change this parameter, the phone will reboot to make the change take effect.
Example: Encrypting Configuration Files
The following example describes how to use “Config_Encrypt_Tool.exe” to encrypt the account.cfg file. For more
information on the other two encryption tools, refer to Yealink Configuration Encryption Tool User Guide.
The way the IP phone processes other configuration files is the same as that of the account.cfg file.
Procedure:
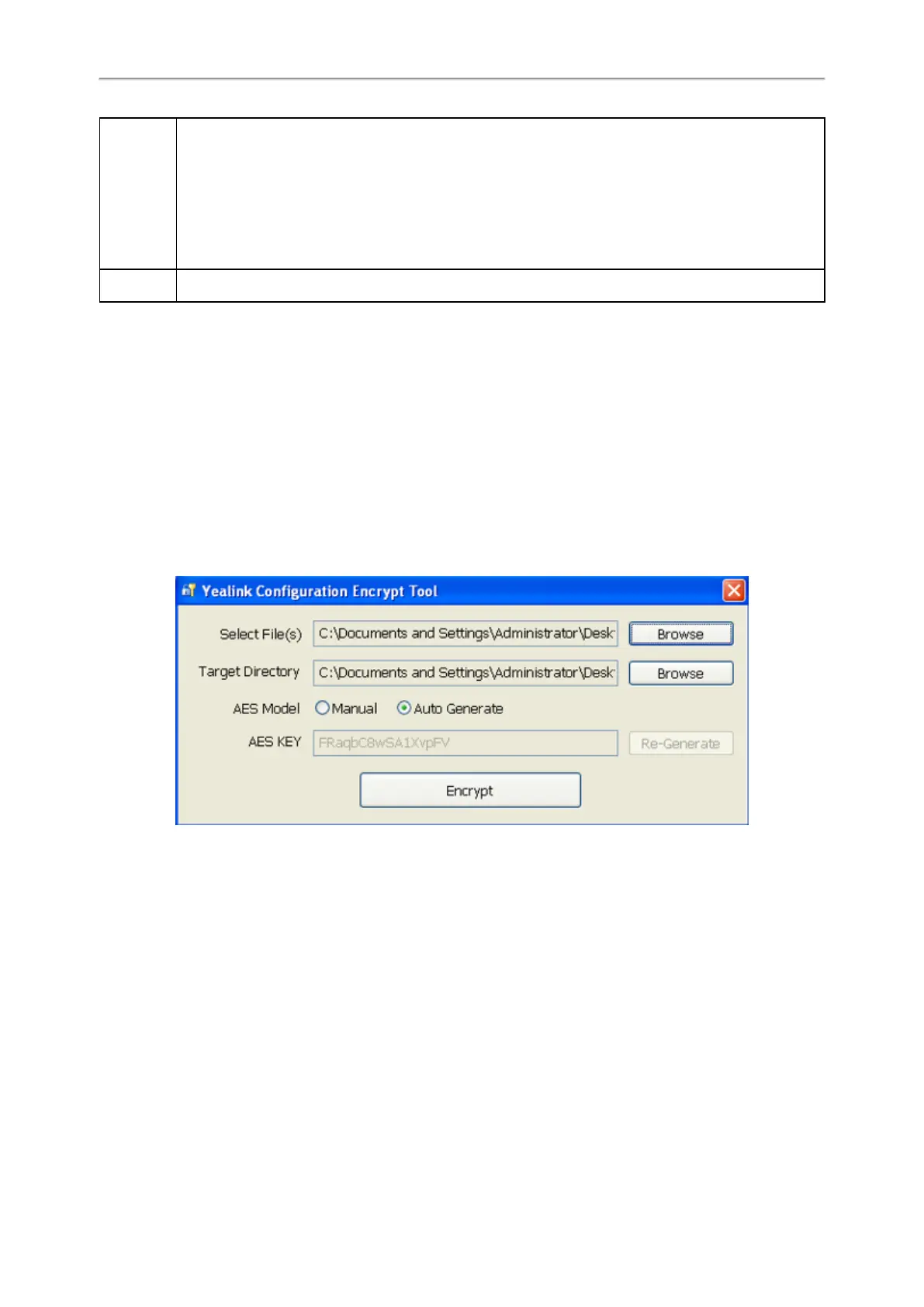
1. Double click “Config_Encrypt_Tool.exe” to start the application tool.
The screenshot of the main page is shown as below:
2. When you start the application tool, a file folder named “Encrypted” is created automatically in the directory where
the application tool is located.
3. Click Browse to locate configuration file(s) (for example, account.cfg) from your local system in the Select File(s)
field.
To select multiple configuration files, you can select the first file and then press and hold the Ctrl key and select
other files.
4. (Optional.) Click Browse to locate the target directory from your local system in the Target Directory field.
The tool uses the file folder “Encrypted” as the target directory by default.
5. (Optional.) Mark the desired radio box in the AES Model field.
If you mark the Manual radio box, you can enter an AES key in the AES KEY field or click Re-Generate to generate
an AES key in the AES KEY field. The configuration file(s) will be encrypted using the AES key in the AES KEY field.
If you mark the Auto Generate radio box, the configuration file(s) will be encrypted using random AES key. The
AES keys of configuration files are different.
 Loading...
Loading...