Version 5.8 139 October 2009
SIP User's Manual 3. Web-Based Management
¾ To apply the loaded certificate for IPsec negotiations:
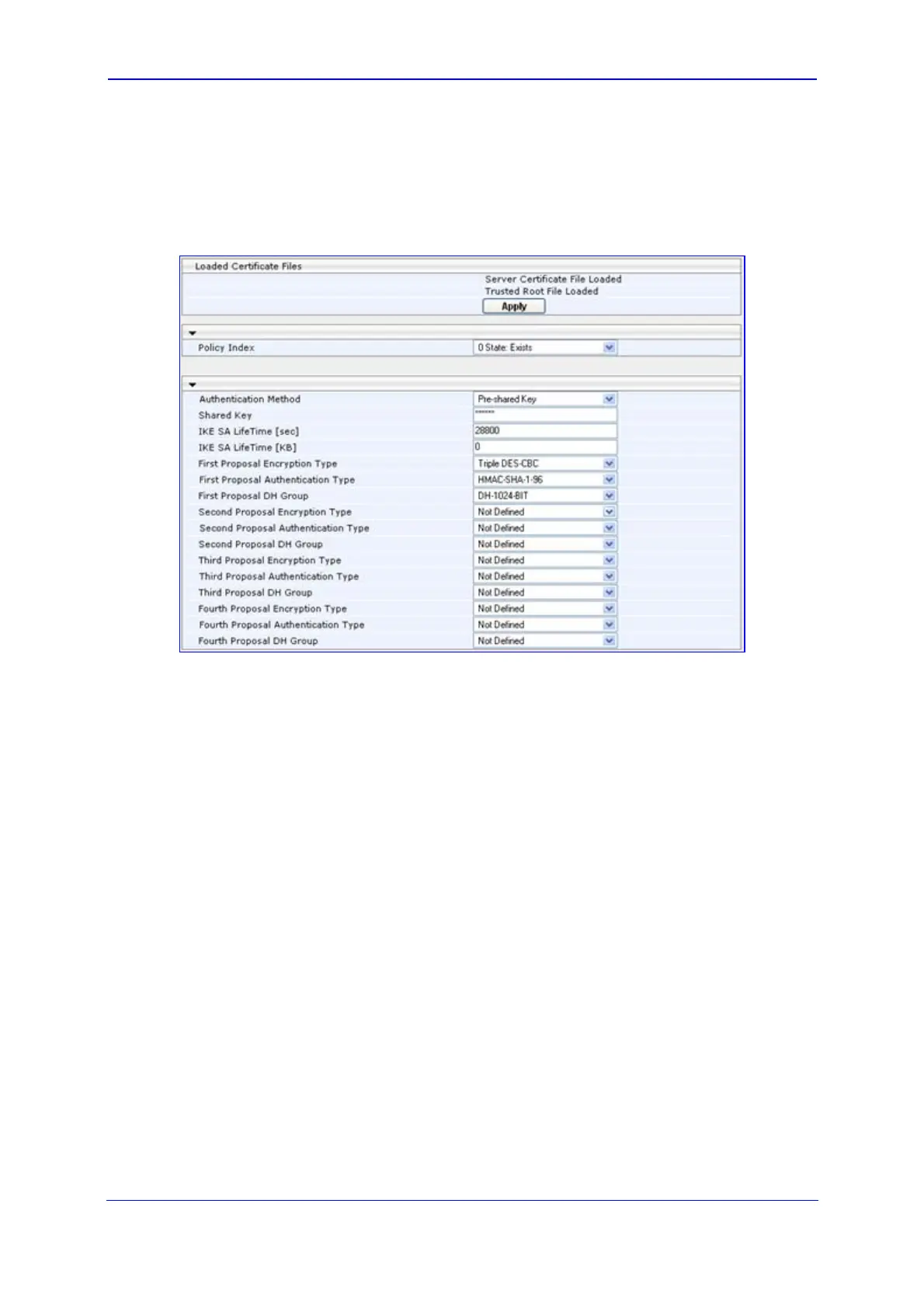
1. Open the ‘IKE Table’ page (refer to Configuring the IKE Table); the 'Loaded
Certificates Files' group lists the newly uploaded certificates, as shown below:
Figure 3-134: IKE Table Listing Loaded Certificate Files
2. Click the Apply button to load the certificates; future IKE negotiations are now
performed using the new certificates.
3.4.4.3.2 Client Certificates
By default, Web servers using SSL provide one-way authentication. The client is certain
that the information provided by the Web server is authentic. When an organizational PKI is
used, two-way authentication may be desired: both client and server should be
authenticated using X.509 certificates. This is achieved by installing a client certificate on
the managing PC, and loading the same certificate (in base64-encoded X.509 format) to
the device's Trusted Root Certificate Store. The Trusted Root Certificate file should contain
both the certificate of the authorized user and the certificate of the CA.
Since X.509 certificates have an expiration date and time, the device must be configured to
use NTP (refer to ''Simple Network Time Protocol Support'' on page 545) to
obtain the
current date and time. Without the correct date and time, client certificates cannot work.
¾ To enable two-way client certificates:
1. Set the parameter 'Secured Web Connection (HTTPS)' to 'HTTPS Only' (0) in
''Configuring the General Security Settings'' on page 141 to en
sure you have a method
of accessing the device in case the client certificate doesn’t work. Restore the previous
setting after testing the configuration.
2. Open the ‘Certificates Signing Request' page (refer to ''Server Certificate
Replacement'' on page 137).
3. In the 'Ce
rtificates Files' group, click the Browse button corresponding to 'Send
"Trusted Root Certificate Store" file ...', navigate to the file, and then click Send File.

 Loading...
Loading...











