Configuring Ethernet Ports MAC Security Overview
OmniSwitch AOS Release 8 Network Configuration Guide December 2017 page 1-28
MAC Security Overview
MACSec (MAC Security) provides point-to-point security on Ethernet links between directly connected
nodes. MACSec prevents DoS/M-in-M/playback attacks, intrusion, wire-tapping, masquerading, and so
on. MACSec can be used to secure most of the traffic on Ethernet links - LLDP frames, LACP frames,
DHCP/ARP packets, and so on.
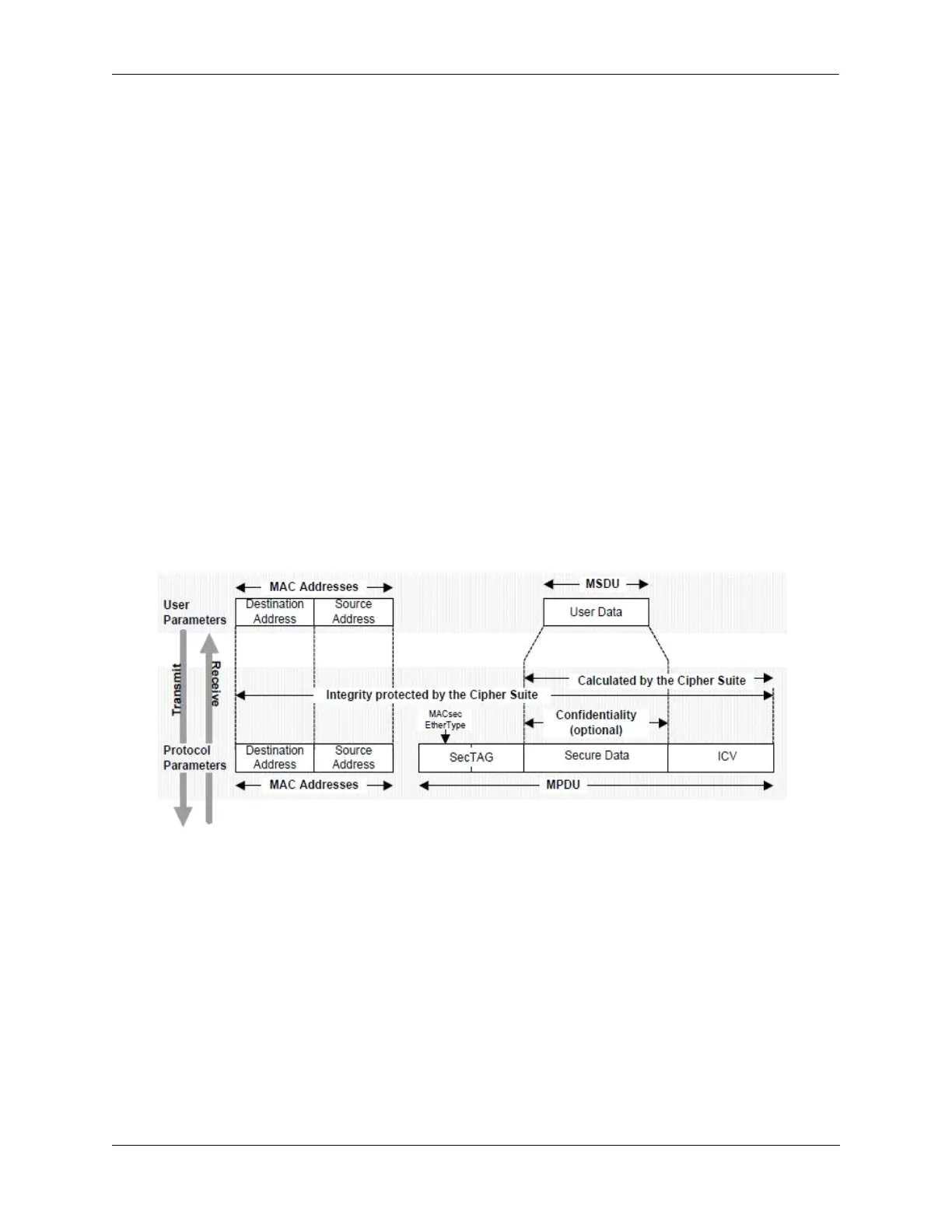
How It Works?
MACSec-enabled links are secured by matching security keys. Data integrity checks are done by
appending an 8-byte or 16-byte header and a 16-byte tail to all Ethernet frames traversing the secured link.
Optionally, traffic can also be encrypted, if enabled by user configuration.
On the wire, a MACSec packet starts with an Ethernet header with etherType 0x88E5, followed by an 8-
byte or 16-byte SecTag header containing information about the decryption key, a packet number and
Secure Channel Identifier. The SecTag header is followed by the payload (which may be optionally
encrypted), and the Integrity Check Value (ICV) generated by GCM-AES of size 16 bytes.
Each node in a MACSec-protected network has at least one transmit secure channel associated with a
Secure Channel Identifier (SCI). Configuration parameters such as enable encryption or perform replay
protection are stored in the context of the transmit secure channel. A single secure channel is
unidirectional - that is, it can be applied to either inbound or outbound traffic.
Each node that expects to receive traffic sent in a particular transmit secure channel must configure a
'matching' receive secure channel, with an SCI corresponding to the SCI of the transmit secure channel of
the peer.
Within each secure channel, secure associations (SA) are defined. The SAs hold the encryption keys
identified by their association number (AN), along with a packet number. On the transmit side, this packet
number is put in the MACSec SecTag header and used in the encryption process. On the receive side, the
packet number from the SecTag header will be checked against the packet number locally stored in the
corresponding secure association to perform replay protection.
MACSec supports two SA (secure associations) modes:
• Static SA Mode
• Dynamic SA Mode

 Loading...
Loading...











