MiCOM P40 Agile P441, P442, P444
4. PX40 CYBER SECURITY IMPLEMENTATION
General Electric IEDs have always been and will continue to be equipped with state-of-the-
art security measures. Due to the ever-evolving communication technology and new threats
to security, this requirement is not static. Hardware and software security measures are
continuously being developed and implemented to mitigate the associated threats and risks.
This section describes the current implementation of cyber security, valid for the release of
platform software to which this manual pertains. This current cyber security implementation
is known as Cyber Security Phase 1.
At the IED level, these cyber security measures have been implemented:
• Four-level Access
• Password strengthening
• Disabling of unused application and physical ports
• Inactivity timer
• Storage of security events (logs) in the IED
• NERC-compliant default display
External to the IEDs, the following cyber security measures have been implemented:
• Antivirus
• Security patch management
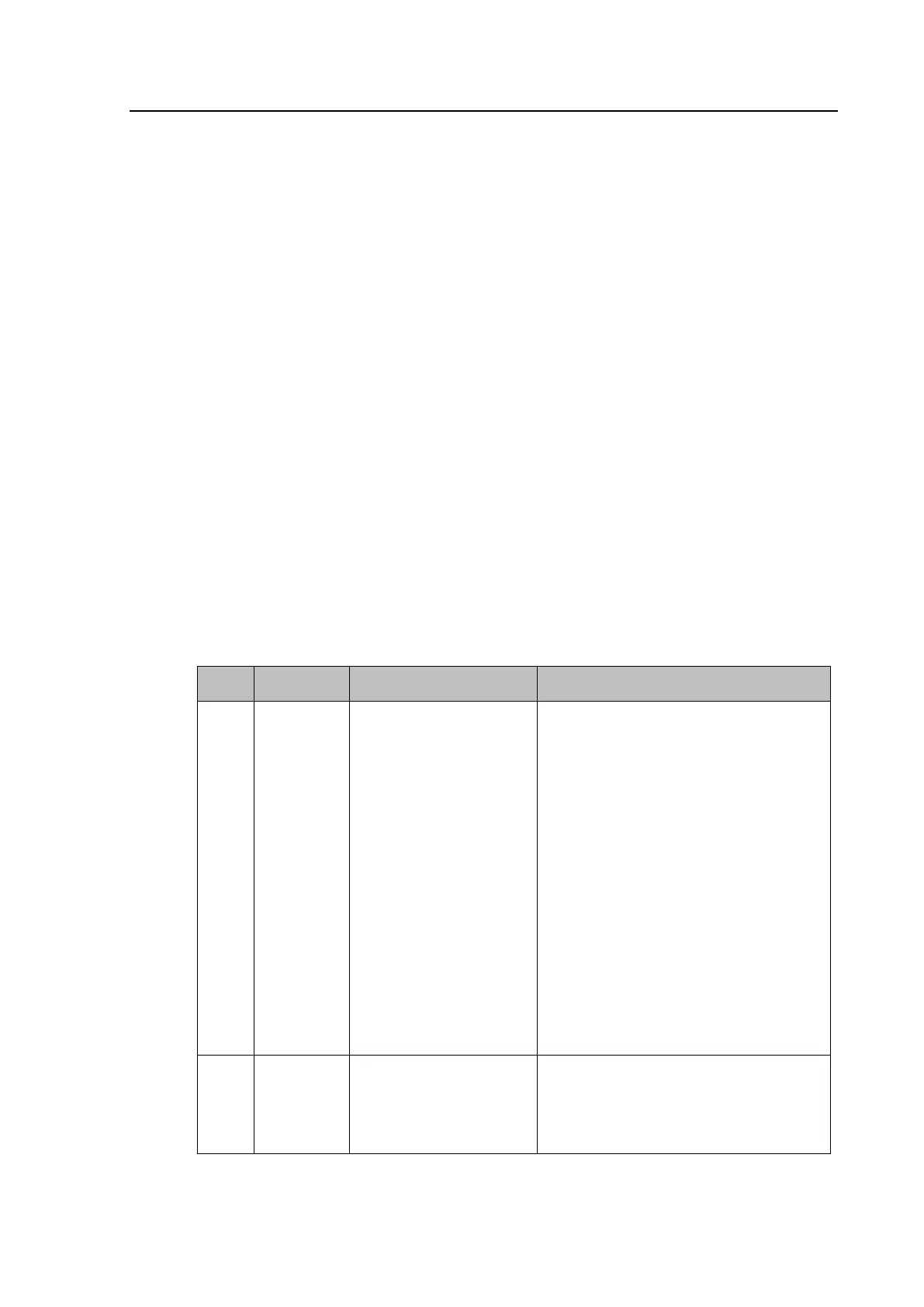
4.1 Four-level Access
The menu structure contains four levels of access three of which are password protected.
These are summarized in Table 3.
Level Meaning Read Operation Write Operation
0 Read Some
Write
Minimal
SYSTEM DATA column:
- Description
- Plant Reference
- Model Number
- Serial Number
- S/W Ref.
- Access Level
- Security Feature
SECURITY CONFIG
column:
- User Banner
- Attempts Remain
- Blk Time Remain
- Fallback PW level
- Security Code (user
interface only)
Password Entry
LCD Contrast (user interface only)
1 Read All
Write Few
All data and settings are
readable.
Poll Measurements
All items writeable at level 0.
Level 1 Password setting
Select Event, Main and Fault (upload)
Extract Events (e.g. via MiCOM S1 Agile)

 Loading...
Loading...