Detecting and Preventing Wireless Intrusion
D-Link Unified Wired and Wireless Access System
July 2012 Page 729
D-Link UWS User Manual
As Figure 443 on page 728 shows, most clients have authenticated with the legitimate AP within the company.
However, one client within the company has unknowingly associated with the honeypot AP that is physically
located outside the walls of the company.
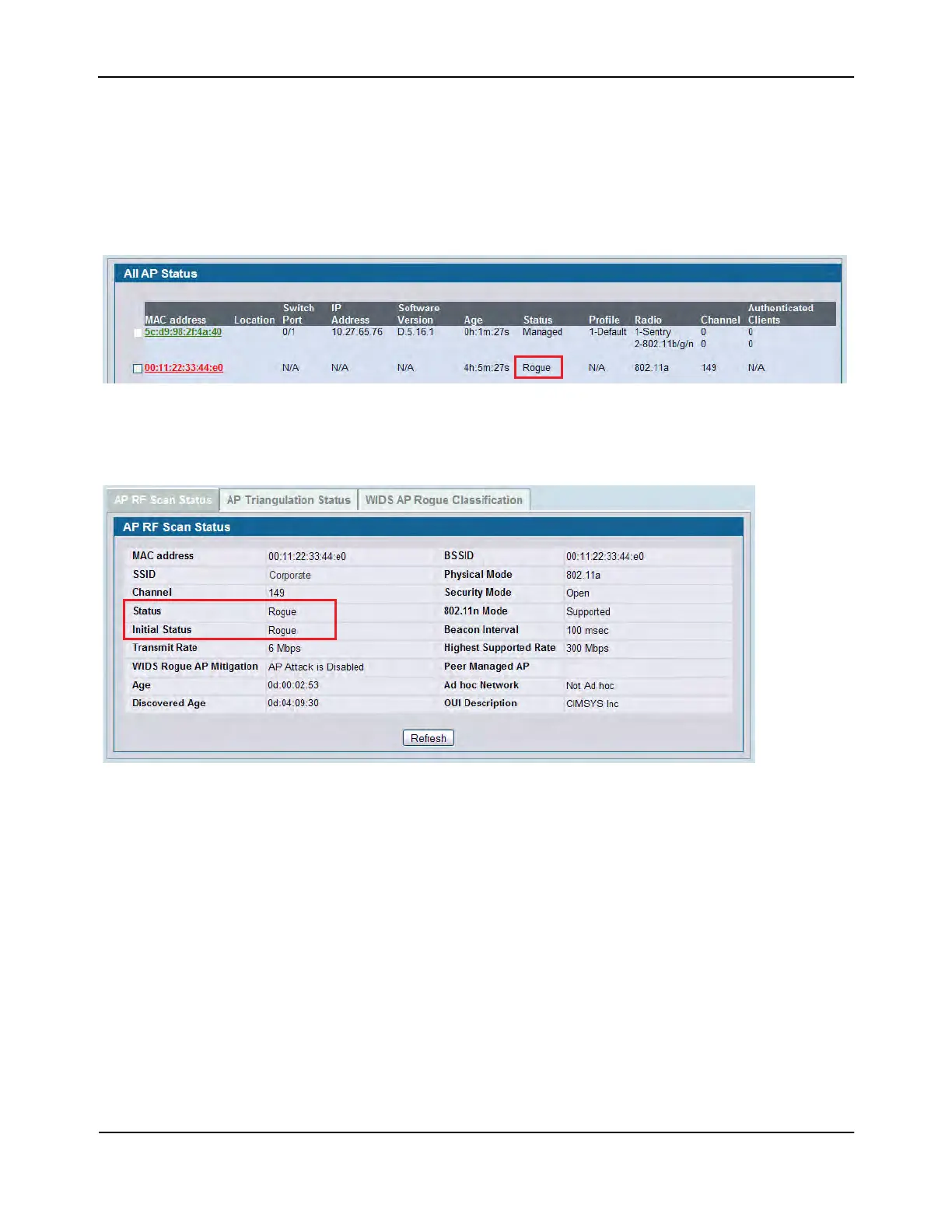
In this situation, the WIDS system on the AP automatically tags the honeypot AP as a Rogue on the WLAN >
Monitoring > Access Point > All AP Status page.
Figure 444: All AP Status with Rogue
Click the MAC address of the rogue AP to view additional information about the AP.
Figure 445: Honeypot AP Rogue Status

 Loading...
Loading...











